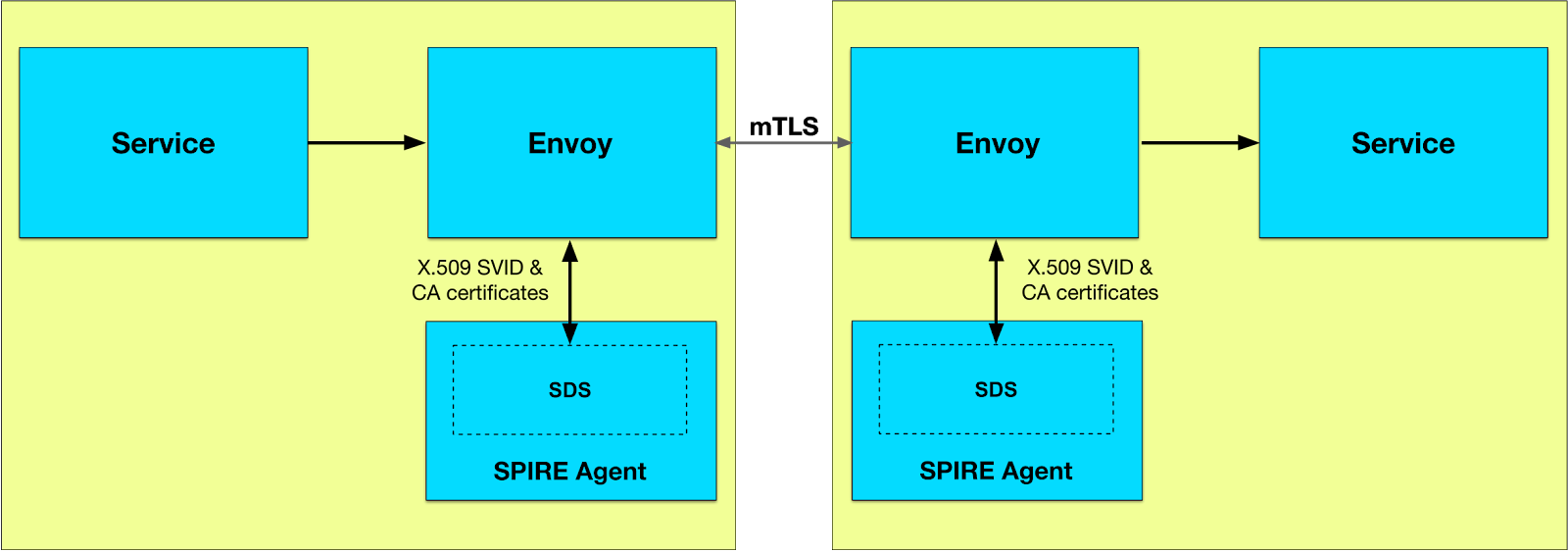
Istio mTLS with SPIRE - How It Works Overview When using Istio with SPIRE, applications communicate using plain HTTP, but the Istio sidecars automatically upgrade connections to mTLS using SPIRE-issued certificates. This provides transparent security without requiring application code changes.
Communication Flow sequenceDiagram participant Curl as curl container(Plain HTTP) participant CurlProxy as curl's istio-proxySPIFFE: spiffe://foo.com/ns/default/sa/curl participant HttpbinProxy as httpbin's istio-proxySPIFFE: spiffe://foo.com/ns/default/sa/httpbin participant Httpbin as httpbin container(Plain HTTP) Curl->>CurlProxy: 1. HTTP Requesthttp://httpbin:8000/headers CurlProxy->>HttpbinProxy: 2. mTLS Handshake(mutual authentication) CurlProxy->>HttpbinProxy: 3. Encrypted mTLS Connection(SPIRE certificates) HttpbinProxy->>Httpbin: 4. HTTP Request(decrypted, localhost) Httpbin->>HttpbinProxy: HTTP Response HttpbinProxy->>CurlProxy: 5. Encrypted Response(adds X-Forwarded-Client-Cert) CurlProxy->>Curl: HTTP Response(decrypted) Step-by-Step Process 1. Application Makes HTTP Request 1 curl http://httpbin:8000/headers The curl container sends a plain HTTP request No TLS, no certificates, no encryption at application level 2. Sidecar Intercepts Request curl’s istio-proxy sidecar intercepts the outbound HTTP request Determines the destination is httpbin service 3. mTLS Handshake curl’s sidecar initiates mTLS connection to httpbin’s sidecar Both sidecars present their SPIRE-issued certificates: curl sidecar: spiffe://foo.com/ns/default/sa/curl httpbin sidecar: spiffe://foo.com/ns/default/sa/httpbin Mutual authentication succeeds using SPIRE trust domain 4. Encrypted Communication HTTP request is encrypted and sent over mTLS connection Only the sidecars handle encryption/decryption Application containers remain unaware of TLS 5. Sidecar Forwards to Application httpbin’s sidecar decrypts the request Forwards plain HTTP to httpbin container on localhost Adds X-Forwarded-Client-Cert header with client identity 6. Response Returns httpbin container sends HTTP response httpbin’s sidecar encrypts it with mTLS curl’s sidecar decrypts and forwards to curl container Evidence of mTLS X-Forwarded-Client-Cert Header 1 2 3 4 5 { "X-Forwarded-Client-Cert": [ "By=spiffe://foo.com/ns/default/sa/httpbin;Hash=...;Subject=\"O=SPIRE,C=US\";URI=spiffe://foo.com/ns/default/sa/curl" ] } This header proves:
...